Online identity theft continues to plague consumers worldwide. While technology enables greater cooperation and sharing, it also exposes that valuable information to increased risk of theft or abuse.
Personal data is constantly proliferating across the digital landscape. As a result, identity theft experiences are on the rise. If you are lucky enough to never have had it happen, it’s only a matter of time.
Due to numerous high-profile data breaches of trusted organizations, and even governments, your information has likely already been exposed. It’s unsettling to think your information is also most likely available on the black market. This may leave you feeling vulnerable because identity theft can often lead to cascading economic, social, and sometimes legal ramifications.
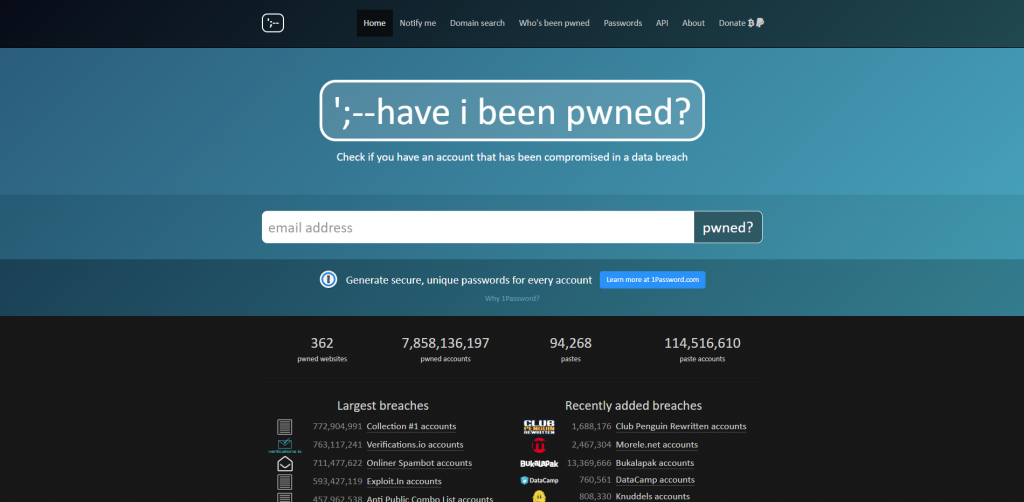
You can check if your email has been exposed quickly on Have I Been Pwned. This is a free online resource that allows you to search on aggregated data breach info.
Mount Your Defense
The best way to protect yourself from this malicious behavior is to mount an active defense. Recognize and take stock of your valuable data both digitally and physically. Then implement sensible safeguards that ensure controls are in place to protect your information.
Treat It Like a Trade Secret
For example, let’s take a look at Coca-Cola. According to court documents from a recent trade secret theft case, the beverage giant takes its famous secret formula very seriously. Workers are routinely subjected to security checks while surveillance cameras dot every corner of the building. In addition, the formula itself is supposedly locked in a multi-million dollar vault. Only two people on Earth have access to it and they fly on separate planes when traveling in case of an accident.
These safeguards are in place because corporate trade secrets do not have the same legal protections as trademarked or patented content. Consequently, they are held in the utmost of confidence to ensure their safety from competitors, criminals, and unauthorized employees.
While all this security and secrecy is likely excessive for your Gmail password or banking credentials, there is no reason the mindset should not be the same. Personal data is just as much your livelihood as any company’s trade secrets. Although this could mean sacrificing the convenience of a sticky note full of passwords next to your desktop, it’s vital to minimize risks with a cautious sense of your own paper and digital trail.
Balancing confidentiality with availability is a key component of risk management strategy and will help inform your choices online.

written by
Alec Simpson
July 2, 2019
Stay informed with industry-relevant emails curated by our team of experts.
We send out emails once or twice a month relating to IP Services, industry news, and events we'll be attending so you can meet our experts in person.

Alec Simpson
Alec Simpson is a trained risk management professional with a keen interest in keeping markets safe and secure for consumers. After earning a degree in Economics, he gathered experience working in the banking & insurance industries before joining the brand protection team at IP Services. Local legends say he is a foosball wizard.